Ricochet Refresh is an open-source project to allow private and anonymous instant messaging
Download


What sets Ricochet Refresh apart:

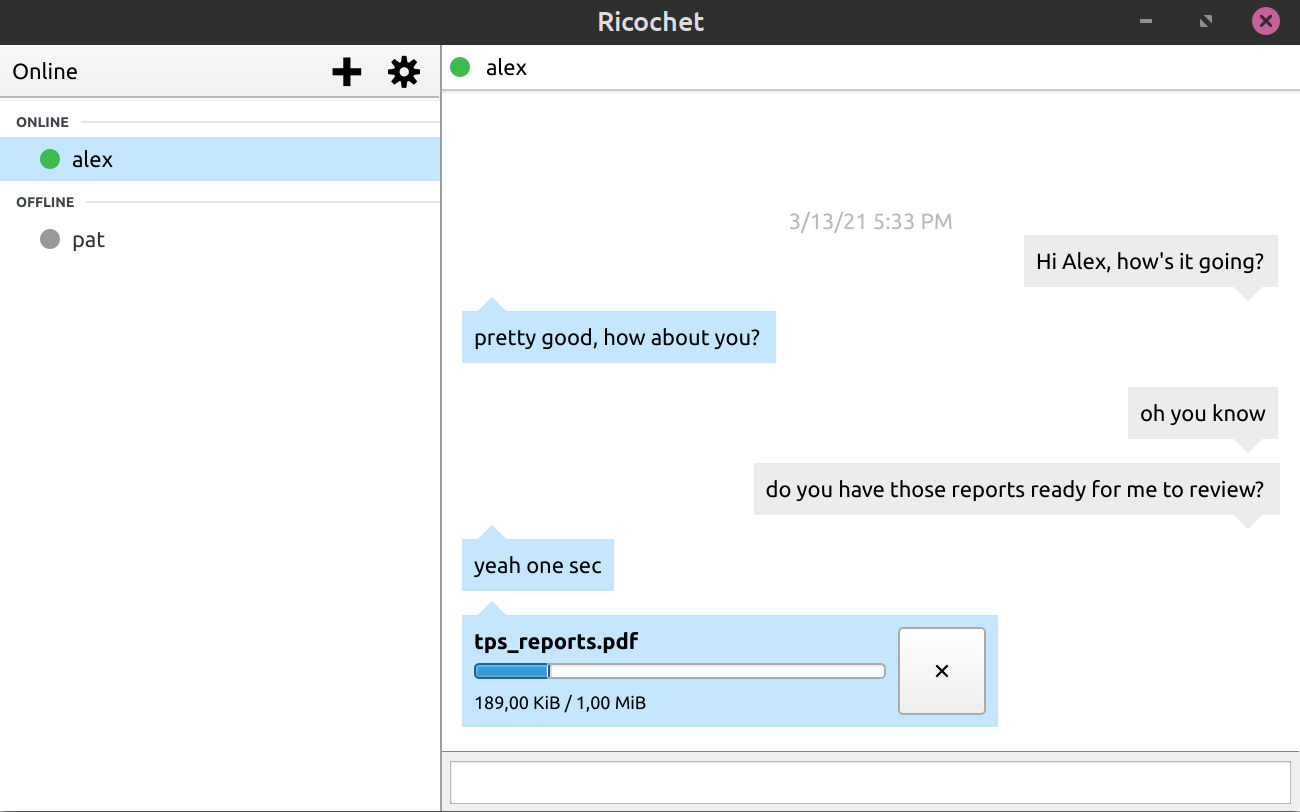
Nobody knows who you talk to or what you say
None of your contacts know your location or IP address
There are no servers to trust, monitor, or hack
Your messages are automatically secure and private
Built-in secure file transfer from within the app
The source code is available for inspection and development
Ricochet was launched in 2014 as a different approach to instant messaging that doesn’t trust anyone in protecting your privacy.
Ricochet Refresh uses the original Ricochet open-source software but has improved on it substantially, such as upgrading its security and making it compatible with Tor Onion Services v3 instead of the older v2.
We believe software like Ricochet is important to protect freedom of expression for whistleblowers, activists, and journalists worldwide.
Ricochet Refresh is a peer-to-peer messenger app that uses Tor to connect clients. When you start Ricochet Refresh it creates a Tor hidden service on your computer. The address of this hidden service is your anonymous identity on the Tor network and how others will be able to communicate with you

To start a chat with someone you need to add the address of their Ricochet Refresh hidden service to your contacts. When you start a chat with one of your contacts a Tor circuit is created between your machine and the your contact's machine. A Tor circuit consists of a series of hops between your machine, Tor nodes, and your contacts machine. It is this use of multiple nodes that provides anonymity, no single node knows both the origin and destination.
To find out more about Tor check out the Tor Overview documentation.
If you are developer and would to like find out more about contributing to Ricohet Refresh please visit our GitHub Repository
Creation of innovative free software needs support. We thank the NGI Assure Fund, a fund established by NLnet with financial support from the European Commission's Next Generation Internet programme, under the aegis of DG Communications Networks, Content and Technology under grant agreement No 957073
Refreshing Ricochet is a big project and we can't do this alone. If you're an open source developer, we want you to help us continue to update and improve Ricochet Refresh.
You can contribute to our GitHub Repository, whether that's with code, by alerting us to bugs you've found, or your suggestions for new features.
Alternatively, if you want to volunteer your time in another way, please contact us.
Below you will find the latest version (3.0.40) of Ricochet Refresh (V3).
If you are developer, or are comfortable compiling from source, the latest sourcecode for V3 can be found on GitHub
All releases are GPG signed by 07AA 9DAA 7088 B94A F3D4 0084 D83A 26FD F505 0FE0
SHA256 Sums
sig
Blueprint for Free Speech is a charity that provides research and analysis in support of freedom of expression for all people, as described the UN Declaration of Human Rights.
To ensure these fundamental rights are upheld, we seek a world where protections for free and independent media, freedom of speech, freedom of information, institutional transparency, and support for whistleblowers, are all enshrined in law.
Find out more about Blueprint for Free Speech at our Website
Several German media news outlets have run a story about law enforcement agencies allegedly breaking the anonymity provided by Tor and, with it, Ricochet-Refresh.
We would like to answer some questions on the matter to clarify the facts from the hype.
We are not aware of any cases where users of the current version of Ricochet-Refresh have been de-anonymised. (Including this alleged case, since no evidence of such was provided to us).
The reported attacks occurred 2019-2021, and we have substantially updated the software to improve security since that time.
Some technical details from our end:
In particular, the vanguards-lite feature was introduced to Ricochet-Refresh in version 3.0.12 in June of 2022, after upgrading to the tor 0.4.7 series. Without being provided with the details of the reported attack, we can not say definitively this feature would have stopped it. However, we do know vanguards were introduced in part to make this general class of attacks more difficult to pull off. Since then, we have continued releasing regular updates which include security updates from our upstream dependencies (including Tor).
Again, we have no proven details of the attack and it's hard to respond to an incident when you can't see the documentation.
'Timing' attacks have been around for a while, nothing new there. They can in theory unmask the identity of an anonymous end-user, but they do not break open the content of a secret conversation. Generally the attacker in this situation would need vast resources and enormous legal powers to be successful - only the kind that a state could access.
The field of cybersecurity rarely offers absolute guarantees. If you want to be perfectly private, you need to disconnect entirely from the digital world. That's not a very practical solution for most people.
So you winnow down risk as far as possible. It's illogical to say 'because there is some very small risk, we should stop using technology to protect ourselves'. Instead, the best choice is to opt for free, open-source software like Ricochet-Refresh, which by design, gives you enormously more privacy and anonymity than the vast majority of other tools.
Ricochet-Refresh is one of the safest ways to communicate online. The vast majority of people using Ricochet-Refresh do not need to do anything to protect themselves against timing analysis attacks.
In the overwhelming majority of cases, an attacker will not be able to find someone's identity because they do not have these kinds of very large resources.
As a purely precautionary measure, we suggest end-users who face powerful attackers should limit the number of people to whom they distribute their Ricochet-Refresh ID. In the context of Ricochet-Refresh, most theoretical and practical attacks are only possible if the adversary knows the ID of the target they are attempting to de-anonymise
Note that the content of the message stays secret in the attack scenarios described to us by the journalist who wrote the story.
We do. We provide monthly(ish) Ricochet-Refresh releases when upstream dependencies (e.g. Tor, openssl, qt, etc) publish security updates. Beyond that, we have also been researching and developing an improved back-end which should make 'timing analysis' attacks much more difficult by providing the user the ability to control their online visibility to unauthorised peers.
Note: Ricochet is not the same as Ricochet-Refresh. Ricochet has been retired because it relies on legacy technology that no longer exists in the Tor Network.
Yes. People should continue using Ricochet-Refresh with a high degree of confidence. It is still one of the most private and secure ways to communicate online.
The protocol is completely peer-to-peer and the client is open-source; there is no account registration, no servers hosting your data, and no centralised organisations or infrastructure to attack. A person's account data is stored locally on their own computer and their communications are only sent to the intended recipients. These communications are private and secure by default because they are end-to-end encrypted.
Contact the team on Twitter: @r2refresh
More information about Blueprint can be found at our website blueprintforfreespeech.net.
You can contact the team at ricochet@blueprintforfreespeech.net. The repository for this website is also on GitHub.